Are you looking for ways to use RemoteIoT behind a firewall on your Mac? In today’s interconnected world, managing IoT devices remotely has become essential for both personal and professional purposes. However, navigating firewalls and ensuring secure connections can be challenging. This article will provide you with a detailed guide on how to use RemoteIoT behind a firewall on your Mac.
RemoteIoT technology allows users to access and control IoT devices from anywhere, making it a powerful tool for automation and monitoring. However, firewalls often pose obstacles, especially on macOS, which has its own built-in security features. Understanding how to configure your system to work seamlessly with RemoteIoT is crucial for maintaining productivity and security.
This guide will walk you through the process step by step, ensuring that you can set up and use RemoteIoT effectively while maintaining a secure connection. Whether you’re a beginner or an advanced user, this article will provide you with the knowledge and tools you need to succeed.
Read also:Understanding The Leo Virgo Cusp Traits Compatibility And Insights
Table of Contents
- Introduction to RemoteIoT and Firewalls
- Understanding Firewalls on Mac
- Setting Up RemoteIoT on Mac
- Configuring Firewall Settings
- Using Port Forwarding for RemoteIoT
- Implementing a Secure Connection with a VPN
- Troubleshooting Common Issues
- Enhancing Security for RemoteIoT
- Best Practices for Using RemoteIoT Behind Firewalls
- The Future of RemoteIoT and Firewalls
Introduction to RemoteIoT and Firewalls
RemoteIoT is a powerful tool that enables users to control and monitor IoT devices remotely. However, firewalls often create barriers, especially on macOS, which has robust security features. Understanding how to navigate these challenges is essential for ensuring smooth connectivity.
Why Use RemoteIoT?
RemoteIoT offers several advantages, including:
- Enhanced control over IoT devices
- Improved efficiency in managing smart home systems
- Increased flexibility for remote work environments
By leveraging RemoteIoT, users can streamline their operations and improve productivity.
Understanding Firewalls on Mac
macOS comes equipped with a built-in firewall that provides an additional layer of security. This firewall can sometimes interfere with RemoteIoT connections, making it necessary to adjust settings.
Key Features of macOS Firewall
The macOS firewall includes features such as:
- Blocking incoming connections
- Allowing specific apps to receive incoming connections
- Stealth mode for enhanced security
Understanding these features is crucial for configuring your system to work with RemoteIoT.
Read also:Exploring The Impact Of Sites Gore A Comprehensive Guide
Setting Up RemoteIoT on Mac
Before configuring your firewall, you need to ensure that RemoteIoT is properly installed on your Mac. Follow these steps to set up RemoteIoT:
- Download the RemoteIoT application from the official website.
- Install the application by following the on-screen instructions.
- Launch the application and create an account if necessary.
Once installed, you can begin configuring your firewall settings to allow RemoteIoT to function correctly.
Configuring Firewall Settings
To use RemoteIoT behind a firewall on your Mac, you need to adjust your firewall settings. Here’s how:
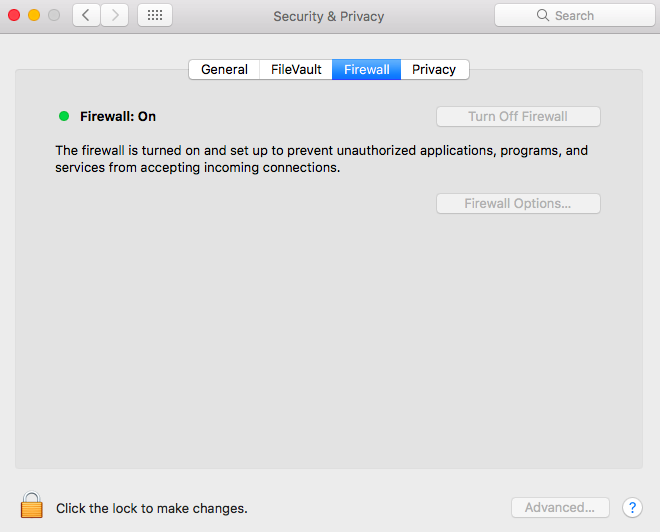
Step 1: Access Firewall Settings
Open System Preferences and navigate to Security & Privacy. From there, select the Firewall tab and click on Firewall Options.
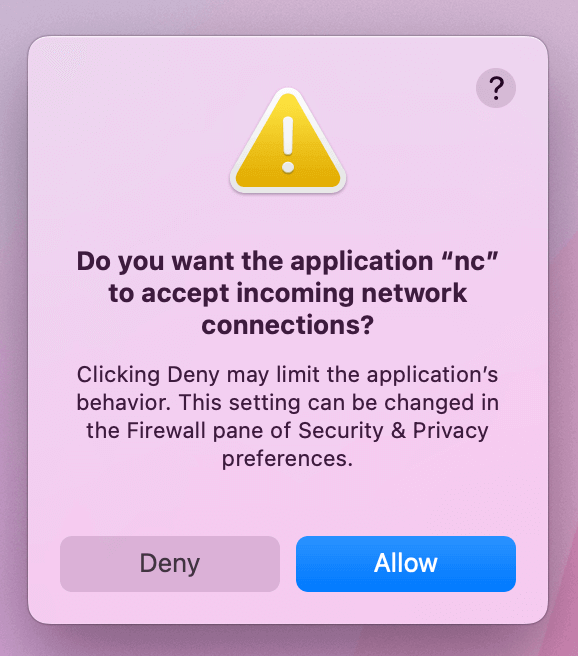
Step 2: Allow RemoteIoT
In the Firewall Options, add RemoteIoT to the list of allowed applications. This ensures that the application can receive incoming connections without being blocked by the firewall.
Using Port Forwarding for RemoteIoT
Port forwarding is a technique used to allow external devices to connect to a device behind a firewall. Here’s how to set up port forwarding for RemoteIoT:
- Access your router’s settings page.
- Locate the port forwarding section.
- Add a new rule, specifying the port number used by RemoteIoT.
By setting up port forwarding, you enable RemoteIoT to communicate with external devices securely.
Implementing a Secure Connection with a VPN
Using a Virtual Private Network (VPN) can enhance the security of your RemoteIoT connection. A VPN encrypts your data, making it difficult for unauthorized users to intercept your communications.
Choosing the Right VPN
When selecting a VPN, consider the following factors:
- Security features
- Speed and performance
- Compatibility with macOS
By implementing a VPN, you can ensure that your RemoteIoT connection remains secure and private.
Troubleshooting Common Issues
Despite careful configuration, issues may arise when using RemoteIoT behind a firewall. Here are some common problems and their solutions:
Problem 1: Connection Issues
If you’re experiencing connection problems, check your firewall settings to ensure that RemoteIoT is allowed. Additionally, verify that port forwarding is correctly configured on your router.
Problem 2: Slow Performance
Slow performance can often be attributed to network congestion or an outdated version of RemoteIoT. Ensure that your application is up to date and consider upgrading your network hardware if necessary.
Enhancing Security for RemoteIoT
Security is paramount when using RemoteIoT behind a firewall. Here are some tips to enhance your system’s security:
- Use strong, unique passwords for all accounts.
- Enable two-factor authentication whenever possible.
- Regularly update your operating system and applications.
By following these best practices, you can protect your data and ensure a secure connection.
Best Practices for Using RemoteIoT Behind Firewalls
Here are some best practices to keep in mind when using RemoteIoT behind a firewall:
- Regularly review your firewall settings to ensure they remain appropriate for your needs.
- Monitor your network for suspicious activity.
- Stay informed about the latest developments in RemoteIoT technology.
Adhering to these practices will help you maintain a secure and efficient RemoteIoT setup.
The Future of RemoteIoT and Firewalls
As technology continues to evolve, the relationship between RemoteIoT and firewalls will become increasingly important. Future developments may include more advanced security features and easier configuration options.
Stay ahead of the curve by keeping up with the latest trends and innovations in RemoteIoT technology.
Conclusion
In conclusion, using RemoteIoT behind a firewall on your Mac is entirely possible with the right configuration. By following the steps outlined in this guide, you can ensure that your system remains secure while allowing RemoteIoT to function effectively.
We encourage you to share your thoughts and experiences in the comments section below. Additionally, feel free to explore other articles on our website for more tips and tricks on managing IoT devices.
References: