In today's interconnected world, managing IoT devices remotely is essential for businesses and individuals alike. However, one common challenge is how to use RemoteIoT behind a firewall on a Mac without exposing your network to potential threats. This article will guide you step-by-step through the process, ensuring you maintain robust security while accessing your IoT devices remotely.
RemoteIoT technology has revolutionized how we interact with smart devices. Whether it's monitoring home automation systems or managing industrial equipment, the ability to control IoT devices from afar is invaluable. However, firewalls often act as barriers, preventing direct access to these devices.
In this article, we will explore practical solutions that allow you to use RemoteIoT behind a firewall on a Mac without compromising your network's integrity. By following the strategies outlined here, you can ensure seamless connectivity while maintaining top-notch security.
Read also:Fran Drescher Rape
Table of Contents
- Introduction to RemoteIoT
- Understanding Firewalls and Their Role
- Configuring Mac for RemoteIoT
- Establishing Secure Connections
- Using Port Forwarding Effectively
- Implementing VPN Solutions
- Leveraging Cloud Services
- Troubleshooting Common Issues
- Best Practices for RemoteIoT Access
- Conclusion
Introduction to RemoteIoT
RemoteIoT refers to the ability to access and manage IoT devices from a remote location. For Mac users, this functionality is particularly useful in both personal and professional settings. However, firewalls often block unauthorized access, making it necessary to implement specific configurations to ensure smooth operation.
Understanding how to use RemoteIoT behind a firewall on a Mac without exposing your network to vulnerabilities requires a combination of technical knowledge and security best practices. This section will provide an overview of the challenges and solutions associated with remote IoT access.
Understanding Firewalls and Their Role
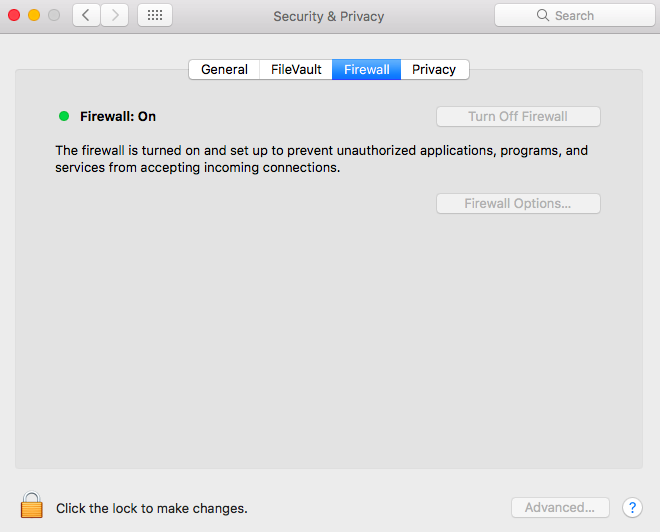
A firewall acts as a barrier between your internal network and external threats. It filters incoming and outgoing traffic based on predefined security rules, ensuring only authorized connections are allowed. While firewalls are essential for network security, they can sometimes hinder remote access to IoT devices.
Types of Firewalls
- Software Firewalls: Installed on individual devices, such as Macs, to protect against unauthorized access.
- Hardware Firewalls: Physical devices that protect entire networks from external threats.
- Cloud Firewalls: Offer scalable protection for cloud-based systems and applications.
By understanding the different types of firewalls and their functions, you can better configure your Mac to work seamlessly with RemoteIoT technology.
Configuring Mac for RemoteIoT
Before attempting to use RemoteIoT behind a firewall, it's crucial to properly configure your Mac. This involves adjusting network settings, enabling necessary services, and ensuring compatibility with IoT devices.
Steps to Configure Your Mac
- Enable Remote Management: Go to System Preferences > Sharing and check the "Remote Management" option.
- Adjust Firewall Settings: Open System Preferences > Security & Privacy > Firewall and customize the rules to allow RemoteIoT traffic.
- Install Required Software: Ensure you have the latest drivers and applications needed for IoT device communication.
Proper configuration ensures your Mac is optimized for RemoteIoT usage while maintaining security.
Read also:Somaliland Wasmo Telegram 2024 A Comprehensive Guide To Understanding Its Impact And Influence
Establishing Secure Connections
Security is paramount when using RemoteIoT behind a firewall. To protect your network and IoT devices, it's essential to establish secure connections using encryption and authentication protocols.
Encryption Protocols
- SSL/TLS: Encrypts data transmitted between your Mac and IoT devices, ensuring privacy.
- SSH: Provides secure shell access for remote command execution.
Implementing these protocols minimizes the risk of unauthorized access and data breaches.
Using Port Forwarding Effectively
Port forwarding allows specific ports to be opened in your firewall, enabling direct communication between your Mac and IoT devices. However, it must be done carefully to avoid exposing your network to potential threats.
Best Practices for Port Forwarding
- Limit Access: Restrict port forwarding to specific IP addresses and devices.
- Monitor Traffic: Regularly review firewall logs to detect and respond to suspicious activity.
By following these guidelines, you can safely use port forwarding to facilitate RemoteIoT access.
Implementing VPN Solutions
A Virtual Private Network (VPN) creates a secure tunnel between your Mac and IoT devices, bypassing firewall restrictions while maintaining privacy. This method is particularly effective for remote access in corporate environments.
Choosing the Right VPN
- Enterprise-grade Solutions: Offer advanced features and scalability for large networks.
- Consumer-grade Options: Provide cost-effective solutions for individual users.
Selecting the appropriate VPN solution ensures secure and reliable RemoteIoT access.
Leveraging Cloud Services
Cloud-based platforms offer an alternative to traditional firewall configurations by hosting IoT devices in a secure, remote environment. This approach simplifies remote access and reduces the need for complex network setups.
Advantages of Cloud Services
- Scalability: Easily accommodate additional devices and users as needed.
- Maintenance: Offload management tasks to experienced cloud providers.
Integrating cloud services into your RemoteIoT strategy can enhance both security and convenience.
Troubleshooting Common Issues
Despite careful planning, issues may arise when using RemoteIoT behind a firewall. Recognizing and addressing these challenges promptly is essential for maintaining seamless connectivity.
Common Problems and Solutions
- Connection Failures: Verify firewall rules and ensure all required ports are open.
- Performance Issues: Optimize network settings and consider upgrading your internet connection.
By troubleshooting effectively, you can minimize disruptions and ensure reliable RemoteIoT access.
Best Practices for RemoteIoT Access
To maximize the benefits of using RemoteIoT behind a firewall on a Mac, it's important to adhere to best practices that prioritize security and efficiency.
Key Recommendations
- Regularly Update Software: Keep your Mac and IoT devices up to date with the latest security patches.
- Implement Multi-factor Authentication: Add an extra layer of protection to your remote access setup.
Following these best practices ensures a secure and efficient RemoteIoT experience.
Conclusion
Using RemoteIoT behind a firewall on a Mac without compromising security is achievable with the right strategies and tools. By understanding firewalls, configuring your Mac properly, and implementing secure connection methods, you can enjoy seamless access to your IoT devices.
We invite you to share your thoughts and experiences in the comments section below. Additionally, explore other articles on our site for more insights into IoT technology and network security.