In today's interconnected world, managing IoT devices behind a firewall using a Mac can be both a challenge and an opportunity for innovation. Whether you're a developer, IT professional, or hobbyist, understanding how to securely connect to remote IoT devices is essential. This guide will walk you through the process step by step, ensuring you can manage your IoT devices efficiently while maintaining robust security.
As more organizations adopt IoT technologies, the need for secure and reliable connectivity has become paramount. Firewalls, while crucial for network security, can sometimes create barriers when trying to access remote IoT devices. However, with the right tools and techniques, you can bypass these obstacles without compromising your network's integrity.
This article will provide you with practical tips, detailed instructions, and expert advice on how to use RemoteIoT behind a firewall using a Mac. By the end of this guide, you'll have the knowledge and confidence to manage your IoT devices effectively, even in the most secure network environments.
Read also:Discovering Keely Coles A Comprehensive Guide To Her Life And Achievements
Table of Contents
- Introduction
- Understanding RemoteIoT
- Firewall Basics
- Why Use Mac for IoT Management
- Step-by-Step Guide to Use RemoteIoT Behind Firewall
- Best Practices for Secure IoT Management
- Common Issues and Troubleshooting
- Security Considerations
- Tools and Resources
- Conclusion
Introduction
In an era where IoT devices are increasingly integrated into our daily lives, managing them remotely is becoming more critical. Whether you're monitoring smart home devices, industrial sensors, or healthcare equipment, the ability to access these devices securely from behind a firewall is essential. This is where RemoteIoT comes in—a powerful tool that allows you to manage IoT devices remotely, even in highly secure network environments.
Using a Mac to manage IoT devices offers several advantages, including a user-friendly interface, robust security features, and compatibility with a wide range of software tools. In this guide, we'll explore how to use RemoteIoT behind a firewall using a Mac, ensuring you can maintain seamless connectivity while adhering to strict security protocols.
Understanding RemoteIoT
RemoteIoT is a cutting-edge solution designed to facilitate secure and efficient remote management of IoT devices. It enables users to monitor, control, and update IoT devices from anywhere in the world, as long as they have an internet connection. The platform supports a wide range of devices and protocols, making it an ideal choice for organizations looking to streamline their IoT operations.
Key Features of RemoteIoT:
- Secure SSL/TLS encryption for data transmission
- Support for multiple protocols, including MQTT, HTTP, and CoAP
- Real-time monitoring and alerts
- Automated device updates and configuration management
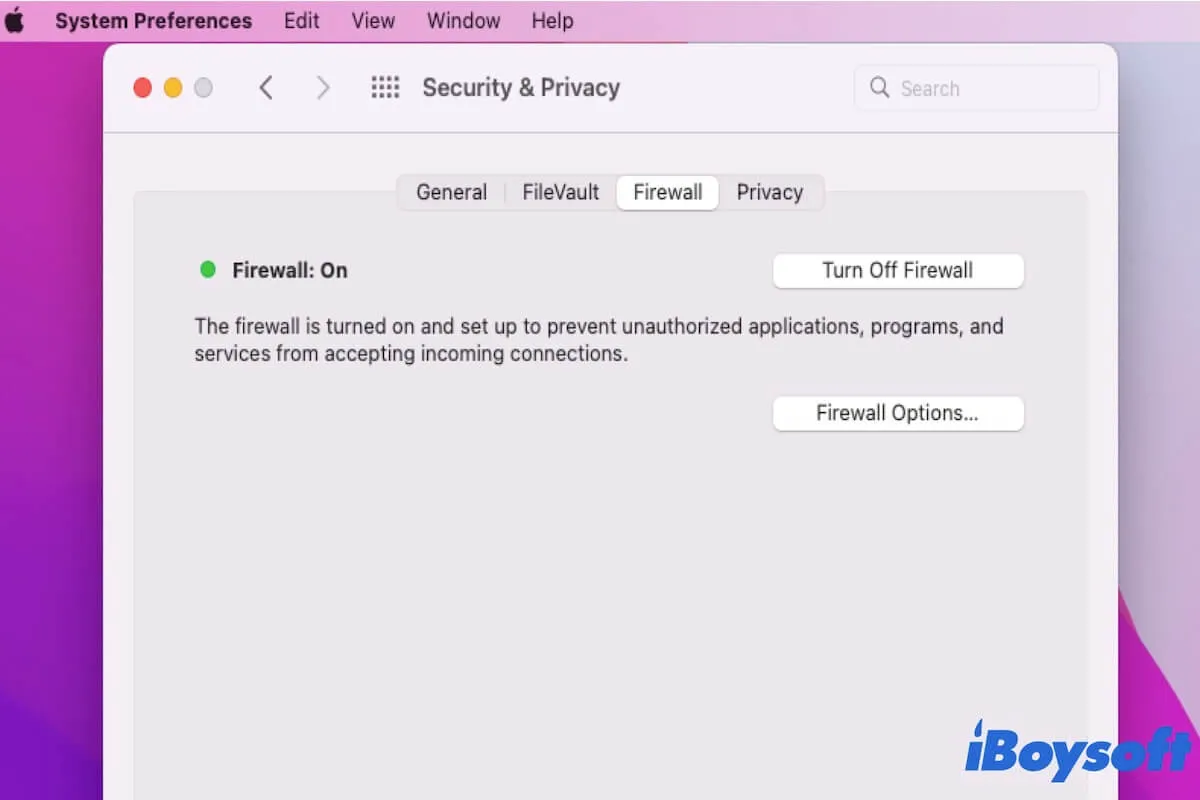
Firewall Basics
A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. Its primary function is to create a barrier between trusted internal networks and untrusted external networks, such as the internet. While firewalls are essential for protecting sensitive data, they can sometimes block legitimate traffic, including connections to remote IoT devices.
Understanding how firewalls work and how to configure them properly is crucial when setting up RemoteIoT behind a firewall. By configuring firewall rules to allow specific traffic, you can ensure secure and uninterrupted connectivity to your IoT devices.
Read also:Mastering Rulz 2023 A Comprehensive Guide To Success
Why Use Mac for IoT Management
Macs are renowned for their stability, security, and ease of use, making them an excellent choice for managing IoT devices. Here are some reasons why using a Mac for IoT management is advantageous:
- Strong built-in security features, such as macOS Gatekeeper and Firewall
- Compatibility with a wide range of development tools and programming languages
- Seamless integration with cloud-based services
- Intuitive user interface for easier device management
Step-by-Step Guide to Use RemoteIoT Behind Firewall
Step 1: Assess Network Requirements
Before configuring RemoteIoT behind a firewall, it's essential to assess your network requirements. Identify the devices you need to manage, the protocols they use, and the ports required for communication. This information will help you configure your firewall rules correctly.
Step 2: Configure Firewall Rules
Configuring firewall rules is a critical step in setting up RemoteIoT behind a firewall. Follow these steps to ensure proper configuration:
- Identify the IP addresses and ports used by your IoT devices
- Create rules to allow incoming and outgoing traffic on these ports
- Test the rules to ensure they work as intended
Step 3: Install Necessary Software
To use RemoteIoT on a Mac, you'll need to install the necessary software. This includes the RemoteIoT client application and any additional tools required for device management. Follow the installation instructions provided by the manufacturer to ensure a smooth setup process.
Step 4: Test Connectivity
Once everything is set up, test the connectivity between your Mac and the remote IoT devices. Use tools like ping and traceroute to verify that traffic is flowing correctly through the firewall. If you encounter any issues, review your firewall rules and make adjustments as needed.
Best Practices for Secure IoT Management
Managing IoT devices securely requires adherence to best practices. Here are some tips to help you maintain a secure and efficient IoT environment:
- Regularly update firmware and software to protect against vulnerabilities
- Use strong, unique passwords for all devices and accounts
- Implement multi-factor authentication for added security
- Monitor network traffic for suspicious activity
Common Issues and Troubleshooting
Even with careful planning, issues can arise when setting up RemoteIoT behind a firewall. Here are some common problems and their solutions:
- Connection timeouts: Check firewall rules and ensure the correct ports are open.
- Authentication errors: Verify username and password credentials.
- Slow performance: Optimize network settings and reduce unnecessary traffic.
Security Considerations
Security should always be a top priority when managing IoT devices. Here are some key considerations to keep in mind:
- Encrypt all data transmissions using SSL/TLS
- Regularly audit network activity for unauthorized access
- Implement network segmentation to isolate IoT devices
Tools and Resources
Several tools and resources can help you manage IoT devices more effectively. Some popular options include:
- Wireshark: A network protocol analyzer for troubleshooting and monitoring traffic
- Postman: A tool for testing APIs and RESTful services
- MQTT.fx: A client application for managing MQTT-based IoT devices
Conclusion
Using RemoteIoT behind a firewall using a Mac is a powerful way to manage IoT devices securely and efficiently. By following the steps outlined in this guide, you can ensure seamless connectivity while maintaining robust security. Remember to adhere to best practices and regularly update your systems to protect against emerging threats.
We encourage you to share your thoughts and experiences in the comments section below. If you found this article helpful, please consider sharing it with others who might benefit from it. Additionally, explore our other resources for more in-depth information on IoT management and security.