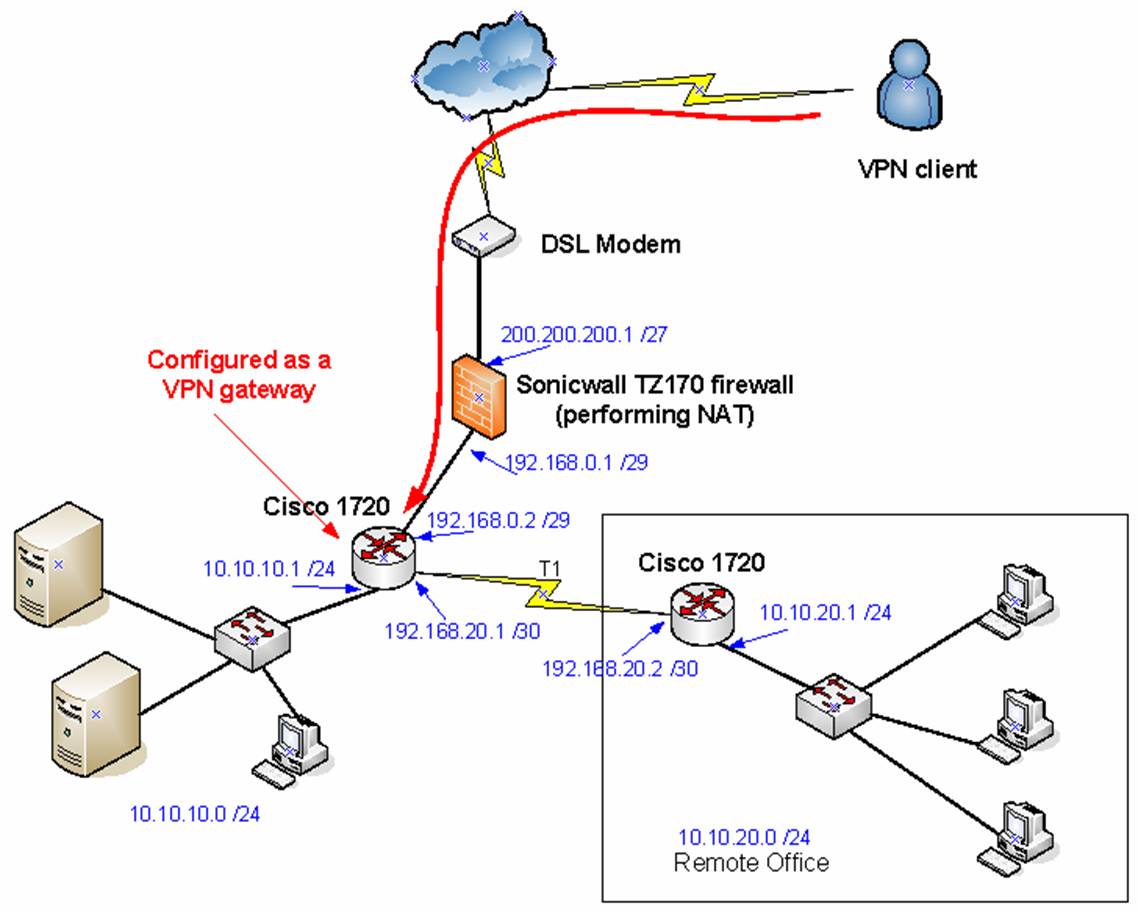
In today's interconnected world, the concept of RemoteIoT behind firewall has become increasingly significant for businesses and individuals alike. As more devices become connected to the Internet of Things (IoT), ensuring secure communication and management of these devices is paramount. RemoteIoT behind firewall offers a solution that allows secure access to IoT devices from anywhere, without compromising network security.
With the rapid adoption of IoT technologies, companies are facing challenges in managing their devices effectively while maintaining robust security measures. This is where RemoteIoT behind firewall comes into play, providing a secure and efficient way to manage IoT devices remotely.
This article will delve into the intricacies of RemoteIoT behind firewall, exploring its benefits, challenges, and best practices. Whether you're a network administrator, IT professional, or simply someone interested in IoT security, this guide will provide valuable insights to help you understand and implement RemoteIoT solutions effectively.
Read also:Discover The Vibrant World Of Wasmo Telegram Nairobi Somali A Cultural Gem
Before we dive into the details, let's take a look at the table of contents to navigate through the various sections of this article.
Table of Contents
- Introduction to RemoteIoT Behind Firewall
- Why Is RemoteIoT Behind Firewall Important?
- Key Components of RemoteIoT Behind Firewall
- Security Considerations for RemoteIoT
- Benefits of RemoteIoT Behind Firewall
- Challenges in Implementing RemoteIoT
- Best Practices for RemoteIoT Deployment
- Tools and Technologies for RemoteIoT
- Real-World Applications of RemoteIoT
- Future Trends in RemoteIoT
- Conclusion
Introduction to RemoteIoT Behind Firewall
RemoteIoT behind firewall refers to the practice of securely managing and accessing IoT devices located within a private network from external locations. This approach ensures that sensitive data remains protected while enabling remote monitoring and control of IoT devices.
As organizations increasingly rely on IoT devices for various operations, the need for secure remote access has become critical. RemoteIoT solutions provide a way to bridge the gap between convenience and security, allowing authorized users to interact with IoT devices without exposing them to external threats.
Some key aspects of RemoteIoT behind firewall include:
- Secure tunneling protocols
- Authentication mechanisms
- Encryption techniques
Why Is RemoteIoT Behind Firewall Important?
Enhancing Security
One of the primary reasons RemoteIoT behind firewall is important is its ability to enhance the security of IoT devices. By keeping devices within a private network and using secure access methods, the risk of unauthorized access and data breaches is significantly reduced.
Improving Efficiency
RemoteIoT solutions allow organizations to manage their IoT devices more efficiently. Administrators can perform tasks such as firmware updates, configuration changes, and troubleshooting without being physically present at the device's location.
Read also:Harper Zilmer Age A Comprehensive Guide To Her Life And Achievements
Cost Savings
Implementing RemoteIoT behind firewall can lead to cost savings by reducing the need for on-site visits and minimizing downtime caused by device malfunctions.
Key Components of RemoteIoT Behind Firewall
Several components work together to enable secure remote access to IoT devices:
- Firewall: Acts as a barrier between the internal network and external threats.
- VPN: Provides a secure tunnel for remote access.
- Authentication Server: Verifies user credentials before granting access.
- Encryption Protocols: Ensures data transmitted between devices and remote users remains secure.
Security Considerations for RemoteIoT
Authentication Mechanisms
Strong authentication mechanisms are essential for ensuring that only authorized users can access IoT devices remotely. Multi-factor authentication (MFA) is often recommended to add an extra layer of security.
Data Encryption
Encrypting data transmitted between devices and remote users is crucial to prevent eavesdropping and data theft. Protocols such as TLS and SSL are commonly used for this purpose.
Intrusion Detection
Implementing intrusion detection systems (IDS) can help identify and respond to potential security threats in real-time, further enhancing the security of RemoteIoT solutions.
Benefits of RemoteIoT Behind Firewall
There are numerous benefits associated with RemoteIoT behind firewall:
- Improved device management capabilities
- Enhanced security and privacy
- Reduced operational costs
- Increased flexibility and scalability
Challenges in Implementing RemoteIoT
Complexity of Setup
Setting up a secure RemoteIoT environment can be complex, requiring expertise in networking, security, and IoT technologies.
Resource Constraints
Limited resources, such as budget and personnel, can pose challenges in implementing and maintaining RemoteIoT solutions.
Compatibility Issues
Ensuring compatibility between different IoT devices and remote access tools can be a challenge, especially in heterogeneous environments.
Best Practices for RemoteIoT Deployment
To ensure a successful RemoteIoT deployment, consider the following best practices:
- Conduct a thorough risk assessment before implementation.
- Use strong authentication and encryption protocols.
- Regularly update and patch all components of the system.
- Monitor system logs for suspicious activities.
Tools and Technologies for RemoteIoT
Several tools and technologies are available to facilitate RemoteIoT behind firewall implementations:
- OpenVPN: A popular open-source VPN solution for secure remote access.
- Zero Trust Architectures: A modern approach to network security that assumes no trust by default.
- IoT Management Platforms: Software solutions designed to manage IoT devices efficiently.
Real-World Applications of RemoteIoT
Smart Manufacturing
In the manufacturing sector, RemoteIoT behind firewall enables engineers to monitor and control industrial IoT devices from remote locations, improving productivity and reducing downtime.
Smart Cities
RemoteIoT solutions are being used in smart city initiatives to manage infrastructure such as traffic lights, streetlights, and waste management systems.
Healthcare
In the healthcare industry, RemoteIoT allows medical professionals to remotely monitor and manage IoT-enabled medical devices, improving patient care and outcomes.
Future Trends in RemoteIoT
As technology continues to evolve, several trends are likely to shape the future of RemoteIoT behind firewall:
- Increased adoption of AI and machine learning for enhanced security and automation.
- Integration with 5G networks for faster and more reliable communication.
- Development of more user-friendly interfaces for easier management of IoT devices.
Conclusion
RemoteIoT behind firewall is a powerful solution that combines the convenience of remote access with the security of a private network. By understanding its key components, security considerations, and best practices, organizations can effectively implement and manage RemoteIoT solutions to enhance their IoT operations.
We encourage you to share your thoughts and experiences with RemoteIoT in the comments section below. For further reading, explore our other articles on IoT security and network management.
Data sources and references: