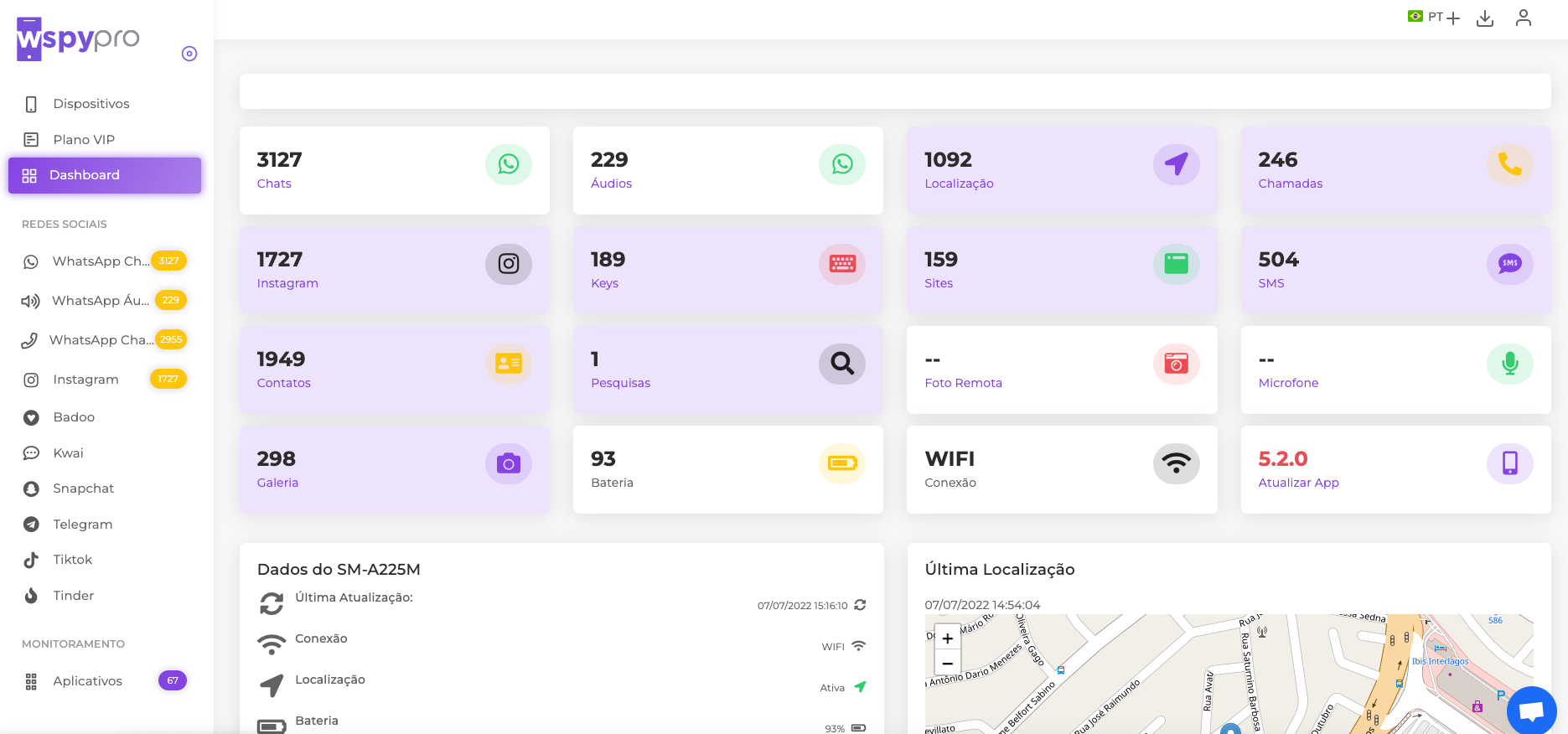
In today's digital age, understanding acronyms like WSPY is crucial for staying informed and ahead of the curve. Whether you're a tech enthusiast, a student, or simply someone interested in learning more about digital tools, this article will provide you with everything you need to know about WSPY. From its origins to its applications, we'll explore every facet of this intriguing concept.
WSPY has gained significant attention in recent years, and for good reason. It represents a powerful tool that can be utilized in various domains, from business to personal use. As we delve deeper into this topic, you'll discover the potential and significance of WSPY in modern technology.
By the end of this article, you'll have a comprehensive understanding of WSPY and how it can impact your life. Let's dive in and explore the world of WSPY together.
Read also:Mastering The Art Of S A Comprehensive Guide To Success
Table of Contents
- What is WSPY?
- History of WSPY
- Types of WSPY
- Benefits of Using WSPY
- Applications of WSPY
- Security and Privacy Concerns
- Legal Considerations
- How to Use WSPY Effectively
- Common Mistakes to Avoid
- The Future of WSPY
What is WSPY?
WSPY refers to a specific type of software or tool designed for monitoring and tracking digital activities. While its exact definition may vary depending on the context, WSPY is generally associated with surveillance and analytics technologies. These tools are used to gather insights, ensure security, and enhance productivity.
One of the primary functions of WSPY is to monitor user behavior on devices such as smartphones, computers, and other connected gadgets. By collecting data, WSPY provides valuable information that can be utilized for various purposes, including business intelligence, parental control, and cybersecurity.
Key Features of WSPY
Here are some of the standout features of WSPY:
- Data collection and analysis
- Real-time monitoring
- Remote access capabilities
- Customizable alerts and notifications
History of WSPY
The origins of WSPY can be traced back to the early days of digital surveillance. As technology advanced, the need for more sophisticated monitoring tools became apparent. Over the years, WSPY evolved from simple tracking software to a comprehensive solution capable of handling complex tasks.
In the late 2000s, WSPY gained popularity as businesses and individuals sought ways to protect their digital assets. The rise of mobile devices and the internet of things (IoT) further fueled the demand for tools like WSPY.
Evolution of WSPY
WSPY has undergone significant changes over the years. Initially, it was primarily used for basic monitoring tasks, but advancements in artificial intelligence and machine learning have expanded its capabilities. Today, WSPY is a versatile tool that caters to a wide range of industries and applications.
Read also:Who Is Camryn Manheim Married To Discover Her Life And Relationships
Types of WSPY
There are several types of WSPY available, each designed for specific use cases. Below are some of the most common types:
- Parental Control WSPY: Used by parents to monitor their children's online activities.
- Business WSPY: Employed by companies to ensure employee productivity and data security.
- Personal WSPY: Utilized by individuals for personal monitoring and protection.
Benefits of Using WSPY
WSPY offers numerous advantages, making it an indispensable tool for many users. Some of the key benefits include:
- Enhanced security through real-time monitoring
- Improved productivity in workplace environments
- Peace of mind for parents concerned about their children's online safety
Additionally, WSPY provides valuable insights that can be used to make informed decisions, whether in business or personal life.
Long-Tail Keywords: Benefits of WSPY in Modern Technology
As technology continues to evolve, the benefits of WSPY become even more pronounced. Its ability to adapt to changing environments ensures that it remains relevant and effective.
Applications of WSPY
WSPY is utilized in a variety of fields, each with its own unique requirements. Some of the most prominent applications include:
- Cybersecurity
- Corporate surveillance
- Parental control
- Law enforcement
Each application leverages the core capabilities of WSPY to address specific challenges and achieve desired outcomes.
Case Study: WSPY in Law Enforcement
In law enforcement, WSPY plays a critical role in investigating crimes and ensuring public safety. By monitoring digital communications and activities, authorities can gather evidence and prevent potential threats.
Security and Privacy Concerns
While WSPY offers numerous benefits, it also raises important questions about security and privacy. Users must be aware of the potential risks associated with its use and take appropriate measures to mitigate them.
Data protection is a top priority when using WSPY. Ensuring that sensitive information is securely stored and transmitted is essential to maintaining trust and compliance with regulations.
Best Practices for Privacy
To safeguard privacy while using WSPY, consider the following best practices:
- Encrypt all data transmissions
- Regularly update software to patch vulnerabilities
- Limit access to authorized personnel only
Legal Considerations
Using WSPY must be done in accordance with applicable laws and regulations. Depending on the jurisdiction, there may be specific requirements regarding consent, data retention, and usage.
It's crucial for users to familiarize themselves with the legal framework governing WSPY to avoid potential liabilities. Consulting with legal experts can help ensure compliance and minimize risks.
Compliance with GDPR
In regions where the General Data Protection Regulation (GDPR) applies, WSPY users must adhere to strict guidelines regarding data collection and processing. Failure to comply can result in significant penalties.
How to Use WSPY Effectively
To maximize the effectiveness of WSPY, follow these steps:
- Define clear objectives for its use
- Select the appropriate type of WSPY for your needs
- Implement robust security measures
- Monitor and analyze data regularly
By following these guidelines, you can ensure that WSPY serves its intended purpose without compromising security or privacy.
Tips for Beginners
For those new to WSPY, here are some tips to get started:
- Start with a small-scale implementation
- Seek training or guidance from experienced users
- Stay updated on the latest trends and developments
Common Mistakes to Avoid
While WSPY is a powerful tool, improper use can lead to unintended consequences. Some common mistakes to avoid include:
- Ignoring security best practices
- Overlooking legal considerations
- Failing to properly configure settings
By being aware of these pitfalls, you can avoid common errors and make the most of WSPY.
The Future of WSPY
Looking ahead, the future of WSPY is promising. Advances in technology, such as artificial intelligence and machine learning, will further enhance its capabilities. As digital landscapes continue to evolve, WSPY will play an increasingly important role in ensuring security and efficiency.
Researchers and developers are continuously exploring new ways to improve WSPY, making it more user-friendly and effective. The potential applications are vast, and the possibilities are endless.
Innovations on the Horizon
Some of the innovations expected in the future include:
- Enhanced AI-driven analytics
- Integration with emerging technologies
- Improved user interfaces
Conclusion
WSPY is a versatile and powerful tool with applications across various domains. From enhancing security to boosting productivity, its benefits are undeniable. However, it's essential to use WSPY responsibly, adhering to best practices and legal requirements.
We encourage you to share your thoughts and experiences with WSPY in the comments below. Additionally, feel free to explore other articles on our site for more insights into the world of technology and digital tools.