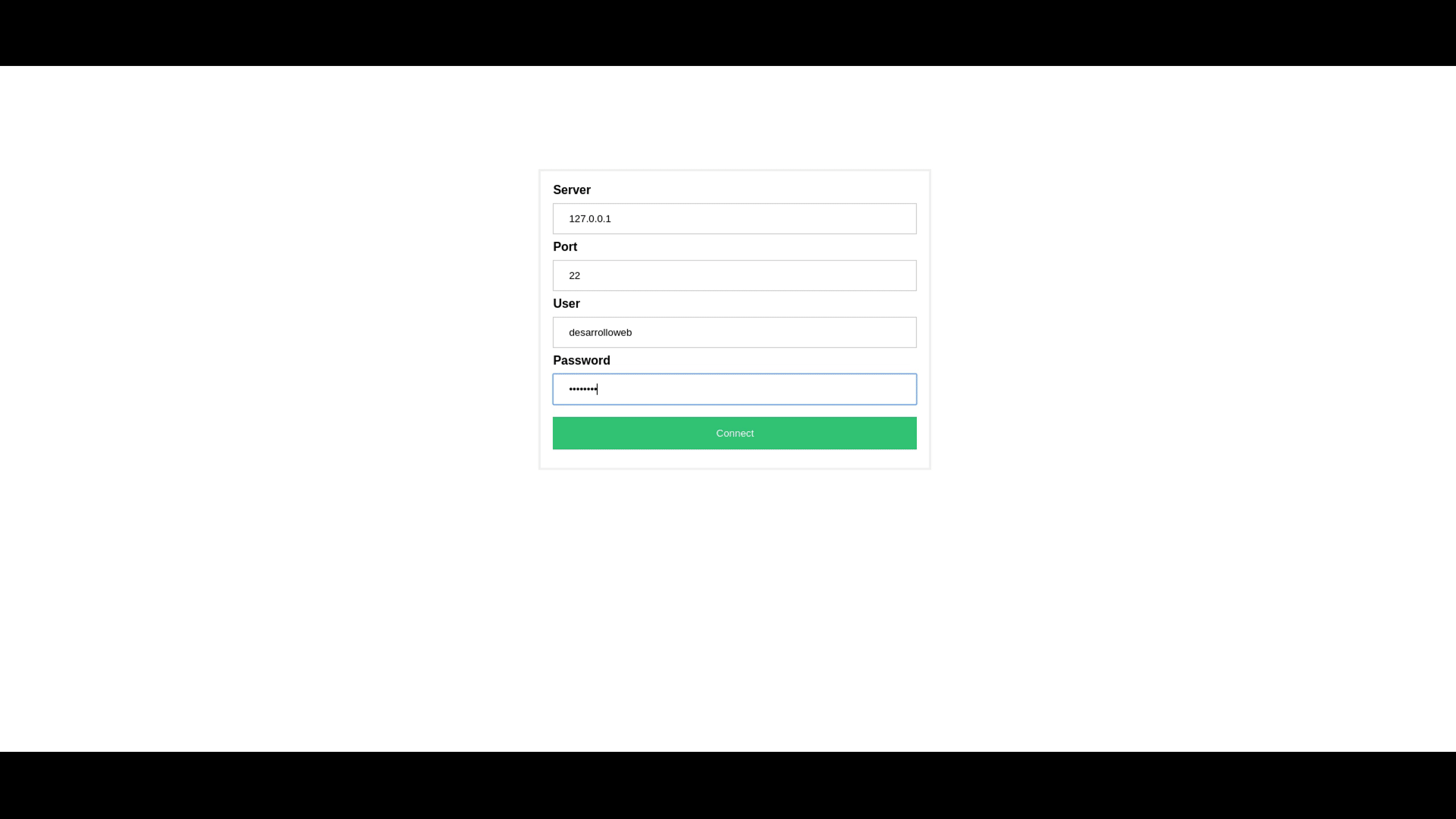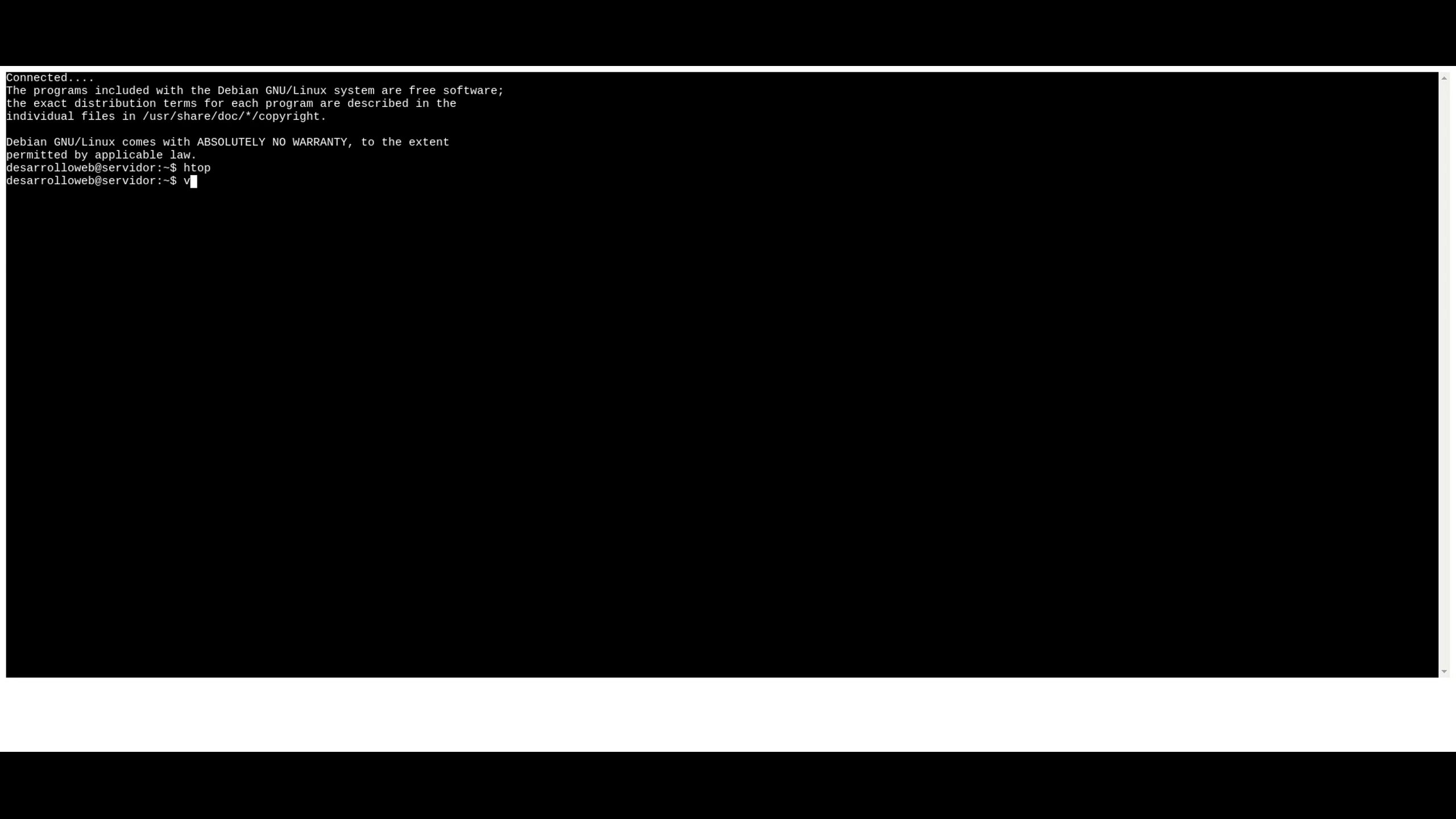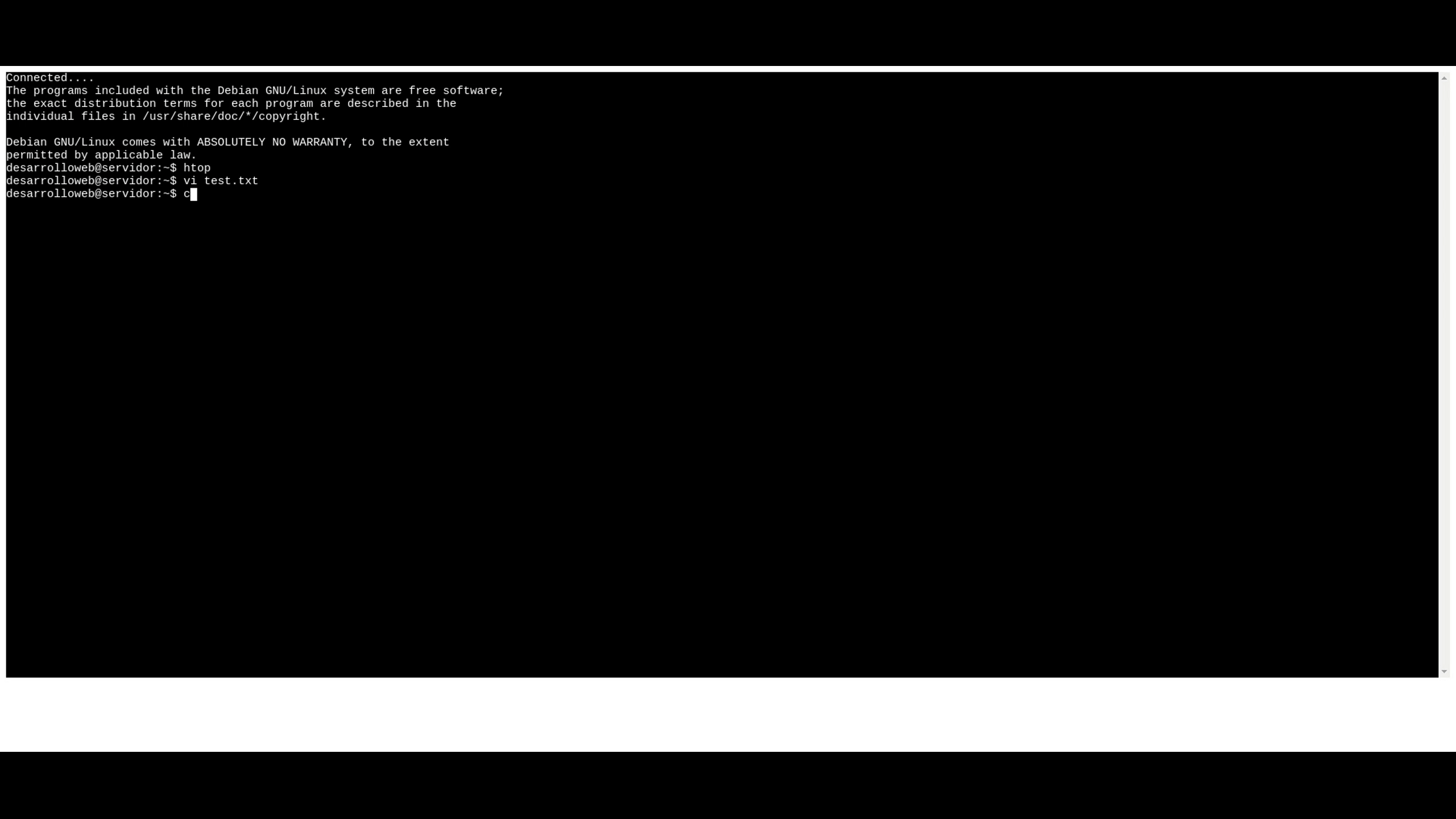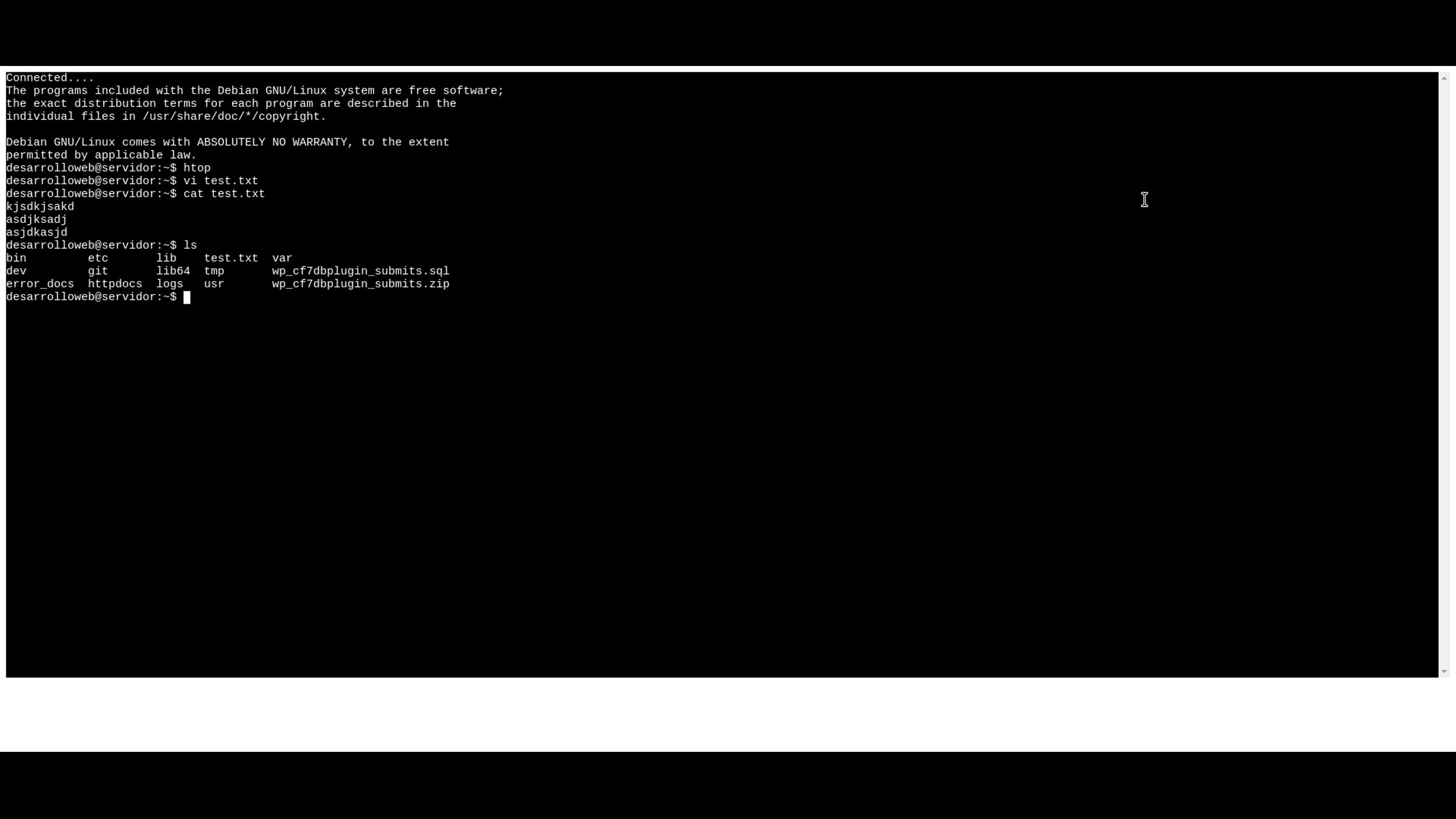
In today's digital age, remote access to devices has become an essential aspect of modern technology. RemoteIoT web SSH offers a powerful solution for securely accessing IoT devices and servers over the internet. This comprehensive guide will provide you with everything you need to know about remote IoT web SSH and its benefits.
As more businesses and individuals adopt IoT devices, the demand for secure remote access solutions has increased significantly. RemoteIoT web SSH plays a critical role in ensuring secure connections between devices and users, making it an indispensable tool in today's interconnected world.
This article will explore the ins and outs of RemoteIoT web SSH, including its advantages, setup process, and best practices. Whether you're a beginner or an experienced professional, you'll find valuable insights and actionable tips to enhance your remote access capabilities.
Read also:Exploring The Donahue Family Pittsburgh Net Worth A Comprehensive Guide
Table of Contents
- Introduction to RemoteIoT Web SSH
- Benefits of Using RemoteIoT Web SSH
- How to Set Up RemoteIoT Web SSH
- Security Features of RemoteIoT Web SSH
- Tools and Software for RemoteIoT Web SSH
- Troubleshooting Common Issues
- Comparison with Other Remote Access Solutions
- Best Practices for RemoteIoT Web SSH
- The Future of RemoteIoT Web SSH
- Conclusion
Introduction to RemoteIoT Web SSH
RemoteIoT web SSH is a cutting-edge solution that allows users to access IoT devices and servers securely over the internet. By leveraging SSH (Secure Shell) protocols, this technology ensures encrypted communication between devices and users, minimizing the risk of unauthorized access.
One of the key advantages of RemoteIoT web SSH is its ability to provide seamless connectivity without the need for complex configurations. This makes it an ideal choice for both individuals and organizations seeking to enhance their remote access capabilities.
Why Choose RemoteIoT Web SSH?
There are several reasons why RemoteIoT web SSH stands out as a top choice for secure remote access:
- Encrypted communication for enhanced security
- Easy setup and configuration
- Compatibility with a wide range of IoT devices
- Cost-effective solution for businesses and individuals
Benefits of Using RemoteIoT Web SSH
Implementing RemoteIoT web SSH in your workflow can offer numerous advantages. Below are some of the most significant benefits:
Enhanced Security
RemoteIoT web SSH utilizes advanced encryption protocols to protect your data during transmission. This ensures that sensitive information remains secure, even when accessed over public networks.
Improved Accessibility
With RemoteIoT web SSH, you can access your IoT devices and servers from anywhere in the world, as long as you have an internet connection. This flexibility allows you to manage your devices efficiently, regardless of your location.
Read also:Christian Slater Botox The Truth Behind The Transformation
Cost Efficiency
Compared to traditional remote access solutions, RemoteIoT web SSH is a cost-effective option. It eliminates the need for expensive hardware and software, making it an attractive choice for businesses of all sizes.
How to Set Up RemoteIoT Web SSH
Setting up RemoteIoT web SSH is a straightforward process that can be completed in a few simple steps. Follow the instructions below to get started:
Step 1: Install SSH Server
The first step is to install an SSH server on your IoT device or server. Most Linux-based systems come with an SSH server pre-installed, but you may need to enable it manually.
Step 2: Configure Firewall Settings
Ensure that your firewall settings allow incoming SSH connections. This typically involves opening port 22 (the default SSH port) on your firewall.
Step 3: Connect Using SSH Client
Use an SSH client, such as PuTTY or OpenSSH, to connect to your device or server. Enter the IP address and login credentials when prompted to establish the connection.
Security Features of RemoteIoT Web SSH
Security is a top priority when it comes to remote access solutions. RemoteIoT web SSH offers several features to ensure the safety of your data:
Encryption
All communication between devices and users is encrypted using advanced algorithms, such as AES and RSA. This ensures that your data remains secure during transmission.
Authentication
RemoteIoT web SSH supports various authentication methods, including password-based and public key authentication. This adds an extra layer of security to your remote connections.
Logging and Monitoring
With RemoteIoT web SSH, you can monitor and log all remote access activities. This allows you to detect and respond to any suspicious behavior promptly.
Tools and Software for RemoteIoT Web SSH
Several tools and software are available to enhance your RemoteIoT web SSH experience. Below are some of the most popular options:
SSH Clients
Popular SSH clients include:
- PuTTY
- OpenSSH
- Termius
SSH Servers
Some widely used SSH servers are:
- OpenSSH Server
- Dropbear
- Bitvise SSH Server
Troubleshooting Common Issues
While RemoteIoT web SSH is a reliable solution, you may encounter some issues during setup or usage. Below are some common problems and their solutions:
Connection Refused
If you receive a "connection refused" error, ensure that your SSH server is running and that the necessary ports are open on your firewall.
Authentication Failed
Double-check your login credentials and ensure that they match the ones configured on your device or server. If you're using public key authentication, verify that the correct key is installed on the server.
Comparison with Other Remote Access Solutions
RemoteIoT web SSH offers several advantages over other remote access solutions. Below is a comparison with some popular alternatives:
TeamViewer
While TeamViewer is user-friendly and feature-rich, it may not offer the same level of security as RemoteIoT web SSH. Additionally, TeamViewer can be more resource-intensive, making it less suitable for lightweight IoT devices.
VNC
VNC provides graphical remote access, but it lacks the encryption and authentication features of RemoteIoT web SSH. This makes it less secure for sensitive applications.
Best Practices for RemoteIoT Web SSH
To maximize the benefits of RemoteIoT web SSH, follow these best practices:
Use Strong Passwords
Create strong, unique passwords for your SSH accounts to prevent unauthorized access. Consider using a password manager to generate and store complex passwords securely.
Enable Two-Factor Authentication
Two-factor authentication adds an extra layer of security to your SSH connections. Enable this feature whenever possible to protect your devices and data.
Regularly Update Software
Keep your SSH server and client software up to date to ensure that you have the latest security patches and features.
The Future of RemoteIoT Web SSH
As the Internet of Things continues to grow, the demand for secure remote access solutions like RemoteIoT web SSH will only increase. Future advancements in encryption, authentication, and connectivity will further enhance the capabilities of this technology, making it an even more valuable tool for businesses and individuals alike.
Conclusion
RemoteIoT web SSH is a powerful and secure solution for accessing IoT devices and servers remotely. By leveraging advanced encryption protocols and authentication methods, this technology ensures the safety of your data while providing seamless connectivity.
We encourage you to implement the best practices outlined in this guide and explore the various tools and software available to enhance your RemoteIoT web SSH experience. Don't forget to share your thoughts and experiences in the comments section below, and feel free to explore other articles on our website for more insightful content.
Data Source: SSH.com, Linux Journal, Cisco